ASUS ZENFONE 6 STOK SORUNU ÇÖZÜLDÜ!
Uzun süredir ülkemizde zincir mağazalarda satışı olan fakat kimse tarafından stok bulunamayan Asus Zenfone serisi ürünlerin en büyük ekranl...
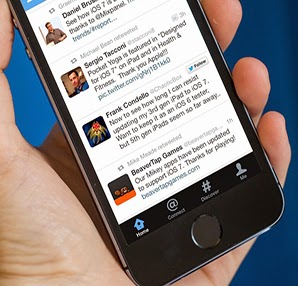 Twitter's innovations to be made irrelevant and uninteresting doubt know that the testing of accounts. This time the test procedure "aleefbaypay" looks like made out of an account named.
Twitter's innovations to be made irrelevant and uninteresting doubt know that the testing of accounts. This time the test procedure "aleefbaypay" looks like made out of an account named.  Threatens many different sectors
Threatens many different sectorsUzun süredir ülkemizde zincir mağazalarda satışı olan fakat kimse tarafından stok bulunamayan Asus Zenfone serisi ürünlerin en büyük ekranl...
 internet
news
technology
Yahoo-Google Co-op!
internet
news
technology
Yahoo-Google Co-op!
Yahoo and Google about e-mail security is a collaboration between the whispers. Two former rivals Yahoo and Google, but the two company...
 internet
news
technology
Twitter's new feature in the test
internet
news
technology
Twitter's new feature in the test
Twitter's innovations to be made irrelevant and uninteresting doubt know that the testing of accounts. This time the test procedure ...
 internet
news
technology
Like us on Facebook collection cycle is closing!
internet
news
technology
Like us on Facebook collection cycle is closing!
Social media giant Facebook, a number of changes in the policies of the previous day Go to the platform announced. According to Facebook...
 internet
news
security
technology
Coca-Cola was hacked
internet
news
security
technology
Coca-Cola was hacked
Israel 's, protesting against the attacks on Gaza Ayyıldız Time Coca-Cola's web sites were hacked. Continuing for days on social m...
 internet
news
technology
PureVPN one of the world's best VPN service is now in Turkish!
internet
news
technology
PureVPN one of the world's best VPN service is now in Turkish!
6 continents and 45 key countries, more than 300 server and the many countries of the particular site and services are unlimited and fast ac...
 internet
news
technology
Badusb name of the new virus may be the greatest threat ever...
internet
news
technology
Badusb name of the new virus may be the greatest threat ever...
If you have Internet viruses, trojans, bad sectors, trojan horses, and you do not even know the name and you'll never know, maybe you ha...
 internet
news
technology
Crouching Yeti still active cyber espionage campaign targets in Turkey are in!
internet
news
technology
Crouching Yeti still active cyber espionage campaign targets in Turkey are in!
Crouching Yeti is still active and also wants to expand the list of victims. Kaspersky Lab, the company's Global Research and Analysis T...
 internet
news
technology
Facebook emergency hotline froze...
internet
news
technology
Facebook emergency hotline froze...
Facebook is the second time within a period of less than two months to collapse, the United States has caused chaos in the city of Los Angel...
 internet
news
technology
Sam Sung company outfit sales pulled
internet
news
technology
Sam Sung company outfit sales pulled
Apple employees creates a great irony of the name of Sam Sung, redundancy and blue uniforms with badges to collect donations for the childre...
 internet
news
software
technology
Internet Explorer plug-in enhances security against
internet
news
software
technology
Internet Explorer plug-in enhances security against
Your internet browser add-ons can be safe, but this does not mean that it is safe against. Microsoft in the Internet Explorer browser to a...
 internet
news
software
technology
Android Wear'a Facebook Messenger desteği
internet
news
software
technology
Android Wear'a Facebook Messenger desteği
Android Developers surprisingly quickly began work on Weir. Now on the market are only two Android-powered device Weir and only 27 percent ...
 internet
news
software
technology
Twitter: Up to countries requesting content removal Turkey
internet
news
software
technology
Twitter: Up to countries requesting content removal Turkey
Between January-June 2014. from Twitter user data, content removal requests and copyright notices Twitter transparency report covering the r...
 game
hardware
internet
mobile
news
security
smart phone
software
tablets
technology
Our site is online
game
hardware
internet
mobile
news
security
smart phone
software
tablets
technology
Our site is online
technology, hardware, software, mobile, internet, news, game, security, tablets, smart phone
